Kubernetes Ingress resource can easily support TLS to handle HTTPS traffic.
All you’ve to do is follow a bunch of steps to enable TLS for your Kubernetes Ingress resource. In this post, I will walk through each of those steps with examples.
In case you are looking to create an Ingress first, check out this post on setting up your first Kubernetes Ingress within a cluster.
Once the Ingress resource is ready, follow the below steps to configure TLS for the same.
1 – Generate a TLS Certificate for the Ingress
To generate a TLS certification, you can use openssl.
First create a private key using the below command:
$ openssl genrsa -out tls.key 2048 This will create the private key file named tls.key.
Using this file, you generate the certificate with the below command:
$ openssl req -new -x509 -key tls.key -out tls.cert -days 360 -subj /CN=kubernetes.docker.internalThe /CN is basically the host name.
This command will create the certificate file named tls.cert.
By the way, if you are interested in Cloud Native architecture and concepts, you’d love the Progressive Coder Newsletter where I explain such concepts in a fun and interesting approach.
Subscribe now and join along.
2 – Create a Kubernetes Secret Resource
In the next step, you have to create the Kubernetes Secret resource using the TLS key and TLS certificate generated in step 1.
$ kubectl create secret tls tls-secret --cert=tls.cert --key=tls.keyHere tls-secret is the name of the Secret resource.
3 – Use the TLS Secret in the Kubernetes Ingress Resource
In this step, you have to update the Ingress object to accept HTTPS requests for a particular host name.
Here’s the YAML file for the Ingress resource that use the TLS certificate.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-demo
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
kubernetes.io/ingress.class: "nginx"
spec:
tls:
- hosts:
- kubernetes.docker.internal
secretName: tls-secret
rules:
- host: kubernetes.docker.internal
http:
paths:
- path: /demo
pathType: Prefix
backend:
service:
name: nodeport-demo
port:
number: 80As you can see, the spec section contains a special section to configure the tls support. The tls-secret is applied to the hostname kubernetes.docker.internal.
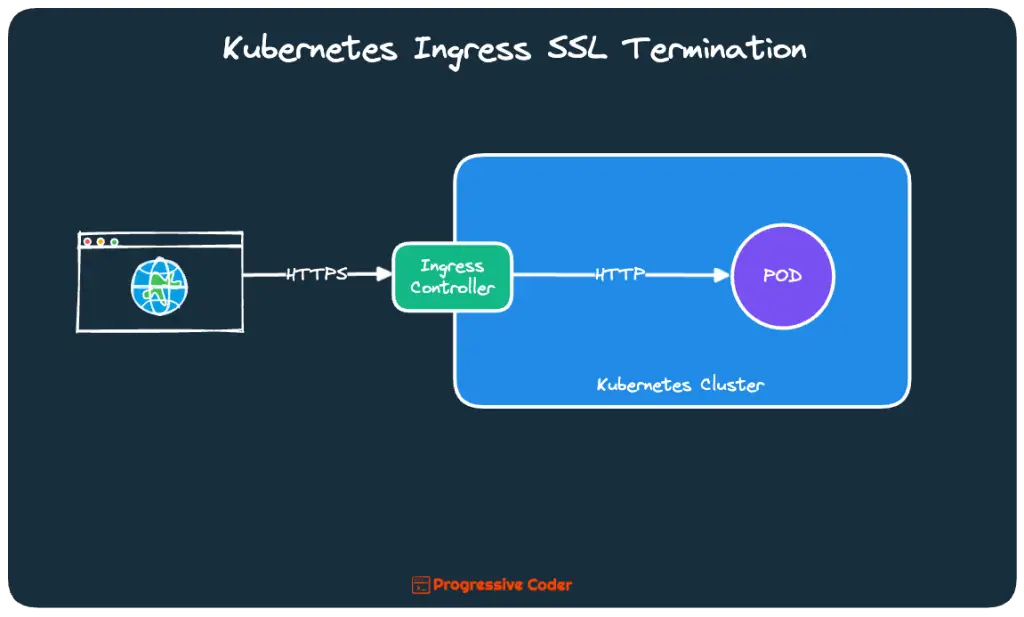
Note that when a client opens a TLS connection to an Ingress controller, the controller terminates the TLS connection.
This means that the client and controller communication is encrypted. However, the communication between the controller and the backend pod is not. This way the application running in the pod doesn’t need to support TLS.
Here’s an illustration that shows the same.
You can now apply the Kubernetes Ingress resource using the below command:
$ kubectl apply -f ingress-demo.yamlIf you now make a curl request to the URL https://kubernetes.docker.internal/demo, you should be able to see the Server Certificate in the output statement.
$ curl -k -v https://kubernetes.docker.internal/demo
* Server certificate:
* subject: CN=kubernetes.docker.internal
* start date: Jul 5 00:55:36 2023 GMT
* expire date: Jun 29 00:55:36 2024 GMT
* issuer: CN=kubernetes.docker.internal
* SSL certificate verify result: self signed certificate (18), continuing anyway.Conclusion
That’s all for this post.
In this post, you got to know the step-by-step process of setting up Kubernetes Ingress with TLS so as to support HTTPS traffic.
If you have any queries or comments, please mention them in the comments section below.
Anyways, before we end this post, a quick reminder about the Progressive Code Newsletter where I explain software concepts using a storytelling approach so that you never forget what you’ve learned. I’m 100% sure you’d love it.
Subscribe now and see you over there.

0 Comments